OS theory concept map
Section 1:
Regarding
operating systems, there are several functions included. An operating is made
up of a user interface, program execution, I/O operations, file system
manipulation, communication, and error detection. These functions are
user-based. System based functions include resource allocation, accounting, as
well as security and protection (Silberschatz, A., Galvin, P. B., & Gagne,
G. 2014).
The
user interface includes one or more functions, which include command line, GUI,
or batch, to call commands to the operating system. Program execution allows
the operating system to start, run, and execute programs. I/O operations allow
the system to operate devices such as a printer. File system manipulation
allows for files to be written and read. Communication allows the operating
system to communicate among the different functions. Error detection detects
and corrects errors within the system, such as a file error or I/O error
(Silberschatz, A., Galvin, P. B., & Gagne, G. 2014).
Resource
allocation allows the operating system to divide up resources to multiple users
that may be using the system. This function allocates memory space, disk space,
or file space. Accounting is another system function that keeps track of the
resources that are being used by different users. The final function is
protection and security, which controls and protects access to the system
resources from outside users (Silberschatz, A., Galvin, P. B., & Gagne, G.
2014).
Figure 1. Operating system
functions
Section 2:
One significant aspect
of an operating system is known as a process. A process is defined as a program
in execution (Silberschatz, A., Galvin, P. B., & Gagne, G. 2014). An
example of a process would be the word application that is being used to type
this assignment. Another process might be the web browser that is up as I
reference information from the course textbook. When describing processes, we
also need to discuss the process state. According to the textbook, as processes
execute, the state the process is in will change. The process may be either
new, running, waiting, ready, or terminated. These include the creation of the
project through completion. (Silberschatz, A., Galvin, P. B., & Gagne, G.
2014). A process control block includes information that is associated with
each process. The PCB includes process state, process counter, CPU registers,
and scheduling information, memory, accounting, and I/O status information
(Silberschatz, A., Galvin, P. B., & Gagne, G. 2014).
Regarding threads,
there are two different options, which include single-threaded and
multi-threaded processes. A single thread is defined as a single unit of CPU
use which can perform one task at a time whereas a multi-thread can perform
multiple tasks (Silberschatz, A., Galvin, P. B., & Gagne, G. 2014). An
example of a multi-thread may be a word processor that can display text as it
is typed while also spell checking. One point to consider when discussing
processes is the critical section problem. When a process is in its critical
section, no other processes can also be in its critical section. If one process
is in its critical section, other processes must wait to enter the critical
section. (Silberschatz, A., Galvin, P. B., & Gagne, G. 2014). A real-life
example of this may be a drive-through car wash. If one car is in the car-wash,
other cars must wait to enter. Once the car wash is complete, the next car may
enter.
Figure 2. Operating system processes.
Section 3:
Regarding
memory and memory management, most would agree memory is one of the most
important aspects of a computer system. Memory management is the functionality
where an operating system moves processes back and forth from the main memory
to disk memory for the processes to execute (Tutorial point, N.D.). Some memory
management functions include address binding where a program is moved from
storage to become a process at some point during the compile, load, or
execution times. Dynamic loading keeps certain routines that are part of a
program on disk memory to utilize more memory space. Swapping includes
processes that are swapped in and out of memory to a backing store, which
allows for more multi programming. Memory allocation involves memory that is
divided into two partitions. These two partitions include low memory for
the operating system and high memory for the user processes (Tutorial point,
N.D.).
Addresses
that are generated by the CPU are known as logical or virtual addresses,
whereas addresses seen by the memory unit are known as physical addresses.
Logical address space is the total set of all logical addresses, whereas
physical address space is the complete set of physical addresses. According to
the text, execution times can differ between logical and physical address
space. Logical addresses must be mapped to physical addresses before they can
be used, and this is done with the memory management unit (Silberschatz, A.,
Galvin, P. B., & Gagne, G. 2014).
Figure 3. Operating system memory management
Section 4:
When discussing files
and file management, we can define this as software that manages data files in
a computer system (Silberschatz, A., Galvin, P. B., & Gagne, G. 2014). The
system organizes the data files to allow easy access. Attributes of a file
include name, identifier, type, location, and protection (Tutorial point,
n.d.). The operations of file management include creating the file where the
file is created in the directory. Reading the file consists of a read pointer
that specifies where the file should be read. Writing a file includes a system
call that specifies the file name and what needs to be written. Deleting a file
locates the file and removes it. Repositioning a file includes setting a file
value to the appropriate entry. The last operation is truncating, where data
from the file is deleted without destroying all file attributes (Silberschatz,
A., Galvin, P. B., & Gagne, G. 2014).
File management
includes various structures which include such as single level, two-level,
tree-structure, acyclic, and graph directories. Single-level directories are
directories where all files are contained in the same directory. Two-level
directories allow each user to utilize their own file directory. Tree structure
directories enable users to create their own sub-directories to organize files.
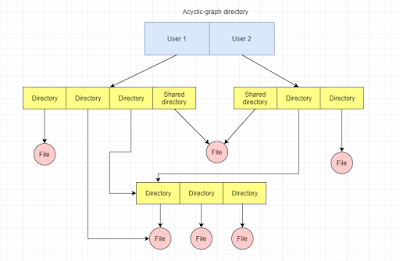
Acyclic graph directories share sub-directories and files. General graph
directories are similar to tree structure directories, but in general graphs,
links are added, and cycles can occur, which dismantles the tree structure
(Silberschatz, A., Galvin, P. B., & Gagne, G. 2014).
Figure 4. Single-level directory
Figure 5 Two-level directory
Figure 6. Tree-structured directory
Figure 7. Acyclic-graph directory
Figure 8. General graph directory
Regarding input and output devices, there are
various options available. The devices are divided between hardware and
software. Some hardware input devices include mouse and keyboards, whereas
output hardware includes monitors, audio, and printers. Input and output
software consist of the device drivers that communicate with the devices,
allowing them to operate. Device drivers are connected to the operating system
and help control the I/O device. The device controller works as an interface
between the device and the device driver and includes electrical components
(Tutorial point. n.d.).
When discussing
protection and security, we can differentiate the two be describing protection
as internal and security external. Within protection, we have domain-based and
language-based. According to the text, domain-based protection gives access
rights that determine how a process operates (Silberschatz, Galvin, &
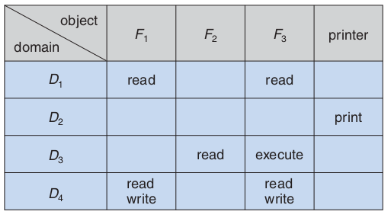
Gagne, 2014). A way we can illustrate how this works is by looking at an access
matrix. An access matrix is a table where the rows are individual domains, and
the columns are objects.
The table will show
which domain has rights on each object. For example, domain one might only be
allowed to read objects two and four, whereas domain three might be able to
read and write on objects one and three (Silberschatz, Galvin, & Gagne,
2014). Language-based protection involves programming languages. These
programming languages include high-level policies that are referenced when
attempting to allocate resources. User-defined system functions, as well as
access to files, are also protected by these programming languages.
(Silberschatz, Galvin, & Gagne, 2014).
As mentioned before,
security is an external aspect. Security protects a system from external
threats. Some of these threats or attacks include Trojan viruses, trap doors,
logic bombs, or stack and buffer overflow. These threats and attacks are
mitigated by several security features such as antivirus software,
cryptography, authentication, encryption, and firewalls (Silberschatz, Galvin,
& Gagne, 2014). These types of security options can be used in tandem with
one another to secure a system further.
Figure 9. Protection vs. security
Summary:
The operating system is
one of the most important parts of a computer system. By definition, a
computers operating system includes system software that manages computer hardware, software resources,
and provides common services for computer programs (Silberschatz, A., Galvin, P. B., & Gagne, G. 2014).
Throughout this course we have discussed many different aspects within an
operating system such as OS functions, processes, memory management File
systems, Mass storage, I/O, as well as Security and protection. We will discuss
a few points regarding these features.
An operating system includes user
interface such as a GUI, program execution, I/O operations, file system
manipulation, communication, and error detection. These functions are
user-based. System based functions include resource allocation, accounting, as
well as security and protection (Silberschatz, A., Galvin, P. B., & Gagne,
G. 2014). Program execution allows the operating system to start, run, and
execute programs. I/O operations allow the system to operate devices such as a
printer. File system manipulation allows for files to be written and read.
Communication allows the operating system to communicate among the different
functions. Error detection detects and corrects errors within the system, such
as a file error or I/O error (Silberschatz, A., Galvin, P. B., & Gagne, G.
2014).
Figure
10. OS user functions
Within
a computer, we have many processes that execute. A process is the instance of
a computer program that is being executed by one or many threads. ... Depending
on the operating system, a process may be made up of multiple threads of execution that
execute instructions concurrently (Silberschatz, A., Galvin, P. B.,
& Gagne, G. 2014). Simply put, a process is a program in execution. as processes execute, the state the process is in will
change. The process may be either new, running, waiting, ready, or terminated. A
process control block includes information that is associated with each
process. The PCB includes process state, process counter, CPU registers, and
scheduling information, memory, accounting, and I/O status information
(Silberschatz, A., Galvin, P. B., & Gagne, G. 2014).
Figure 11. Single threaded process
Memory
management is the functionality where an operating system moves processes back
and forth from the main memory to disk memory for the processes to execute
(Tutorial point, N.D.). Some memory management functions include address
binding where a program is moved from storage to become a process at some point
during the compile, load, or execution times. Dynamic loading keeps certain
routines that are part of a program on disk memory to utilize more memory
space. Swapping includes processes that are swapped in and out of memory to a
backing store, which allows for more multi programming. Memory allocation
involves memory that is divided into two partitions. These two partitions
include low memory for the operating system and high memory for the user
processes (Tutorial point, N.D.).
Figure 12.
Process swapping
File management
includes actions where the system organizes the data files to allow easy
access. Attributes of a file include name, identifier, type, location, and
protection (Tutorial point, n.d.). The operations of file management include
creating the file where the file is created in the directory. Reading the file
consists of a read pointer that specifies where the file should be read.
Writing a file includes a system call that specifies the file name and what
needs to be written. Deleting a file locates the file and removes it.
Repositioning a file includes setting a file value to the appropriate entry.
The last operation is truncating, where data from the file is deleted without
destroying all file attributes (Silberschatz, A., Galvin, P. B., & Gagne, G.
2014).
File management
includes various structures which include such as single level, two-level,
tree-structure, acyclic, and graph directories. Single-level directories are
directories where all files are contained in the same directory. Two-level
directories allow each user to utilize their own file directory. Tree structure
directories enable users to create their own sub-directories to organize files.
Acyclic graph directories share sub-directories and files. General graph
directories are similar to tree structure directories, but in general graphs,
links are added, and cycles can occur, which dismantles the tree structure
(Silberschatz, A., Galvin, P. B., & Gagne, G. 2014). Mass storage may be
handles by a hard disk drive or an external device such as a hard drive. I/O operations
such as printing are handled by device controllers and drivers.
Figure 13. User within double level directory
Two mechanisms used to
control access to a computers programs and resources is protection and
security. Protection can be thought of as an internal mechanism where as
security is external. Within protection, we have domain-based and
language-based. According to the text, domain-based protection gives access
rights that determine how a process operates (Silberschatz, Galvin, &
Gagne, 2014). A way we can illustrate how this works is by looking at an access
matrix. An access matrix is a table where the rows are individual domains, and
the columns are objects.
Figure 14. Access control matrix
Security protects a
system from external threats. Some of these threats or attacks include Trojan
viruses, trap doors, logic bombs, or stack and buffer overflow. These threats
and attacks are mitigated by several security features such as antivirus
software, cryptography, authentication, encryption, and firewalls
(Silberschatz, Galvin, & Gagne, 2014).
Given everything
learned throughout this course, I feel as if I will benefit greatly. Regarding
my career, I currently work for Comcast business. I work on a computer system
everyday and having the knowledge behind the operating system is great
knowledge to have. Furthermore, I am planning to transition into a position in information
technology upon completion of my degree at Ashford university. I recently participated
in a job shadow with the I.T. department at Comcast and was exposed to many of
the departments job functions which included general repair and maintenance of
company issues laptops. These repairs included deep dive into the systems
operating systems. The information covered in this course allowed me the
ability to understand what the I.T. techs were doing as they worked on these systems.
References
File System Management. (n.d.).
Retrieved from https://www.tutorialspoint.com/File-System-Management
Operating system – Services (Links to an external site.). (n.d.).
Retrieved from https://www.tutorialspoint.com/operating_system/os_services.htm
Operating Systems-Memory
Management. (n.d.). Tutorial Point. Retrieved from https://www.tutorialspoint.com/operating_system/os_memory_management.htm
Operating system – I/O hardware.
(n.d.) Retrieved from
https://www.tutorialspoint.com/operating_system/os_io_hardware.htm
Operating system – I/O softwares.
(n.d.). Retrieved from https://www.tutorialspoint.com/operating_system/os_io_software.htm
Silberschatz, A.,
Galvin, P. B., & Gagne, G. (2014). Operating system
concepts essentials (2nd ed.). Retrieved from https://redshelf.com/












Excellent blog.
ReplyDeleteLt-Et Ramya font free download
Periyar font tamil free download